Create a Personal Forensics Lab Part 3: The Windows 10 Workstation
If you haven’t already, complete parts one and two of this guide on building a personal forensics lab in the cloud, which cover creating the Windows Server 2016 primary domain controller (DC), DHCP and DNS server, and the Windows Server 2012 R2 secondary DC.
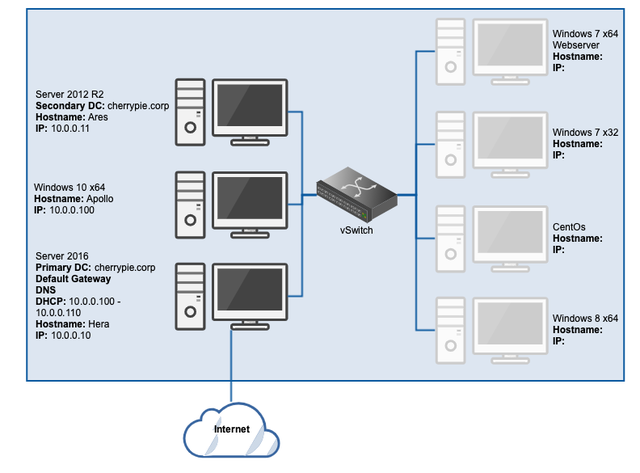
At this point, the lab should look like this:
I’ve chosen to put a single Windows 10 x64 workstation in the environment, but there may be value in adding a 32-bit version as well. There are some things that may only work on one or the other, and it could be interesting to see how forensic artefacts might behave differently between the two versions of the same OS (which is why there are two Windows 7 workstations planned).
It’d be great to get some alternative OSs in the lab, too, most notably macOS, but I’ve found it super difficult to get that running on anything but Apple hardware (which is by design).
Workstation Configuration
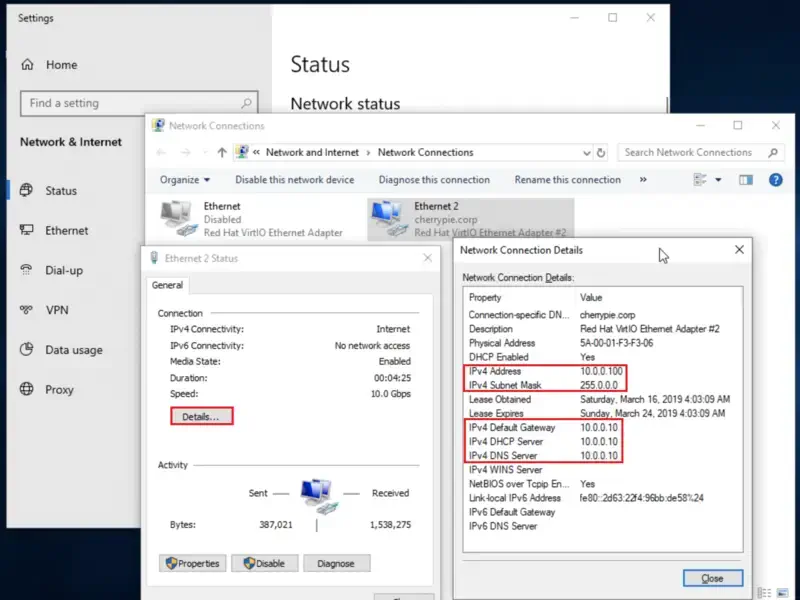
As before, we’ll begin from the freshly installed base OS. With the primary and secondary DCs configured, as well as DHCP and DNS, this machine should automatically get assigned an IP, likely 10.0.0.100 (the first available in the DHCP scope).
Check this in the private NIC details via Network and Internet Settings:
Don’t forget to disable the public-facing NIC. With this automatic configuration, we should be able to access the primary and secondary DCs, and the Internet:
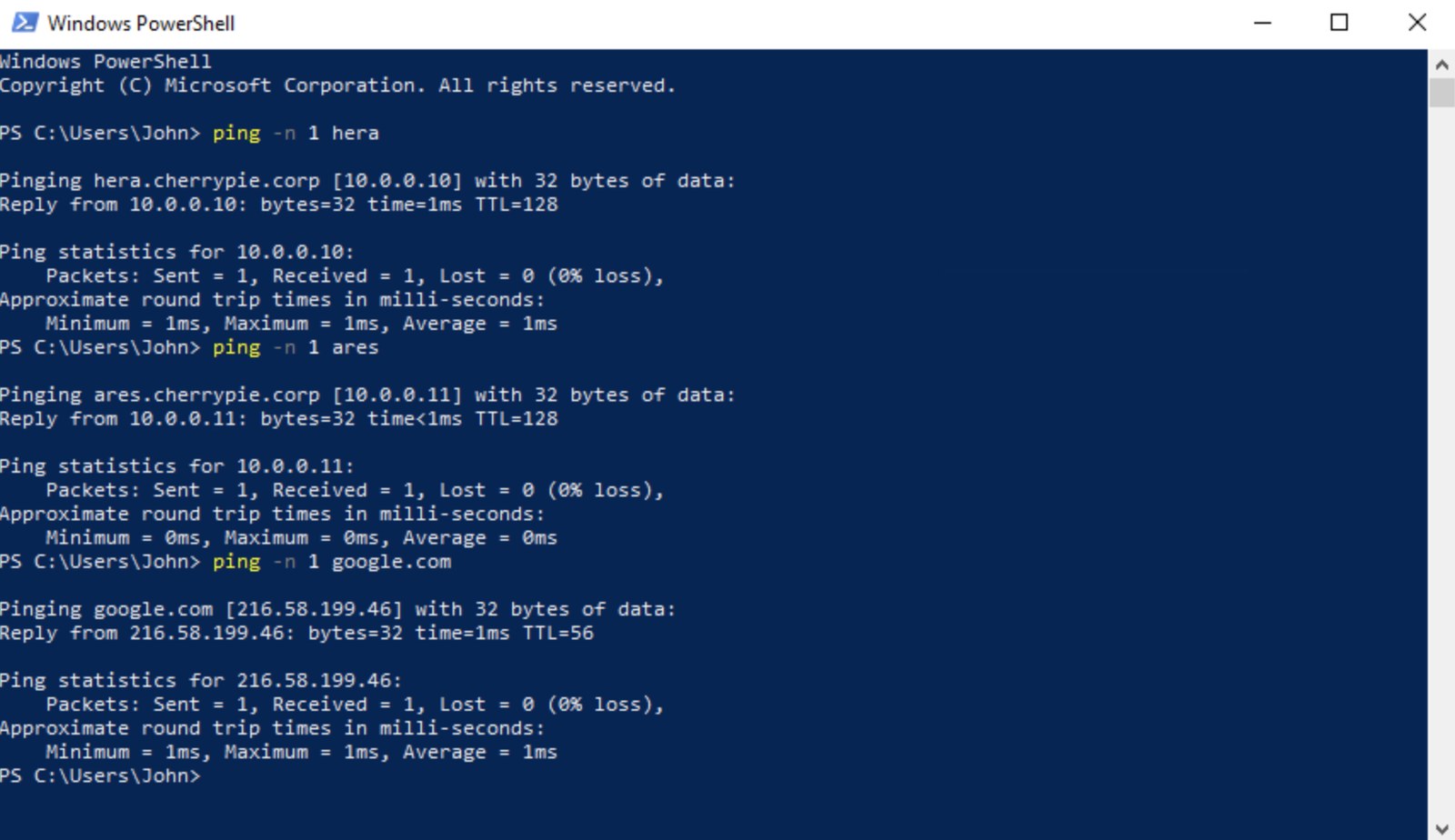
With that confirmed, all we need to do is connect the workstation to the domain, update it, then it’s ready for production (or testing, as the case may be).
Domain Configuration
The easiest way to open the System settings is to right-click the Start Menu, then click System:
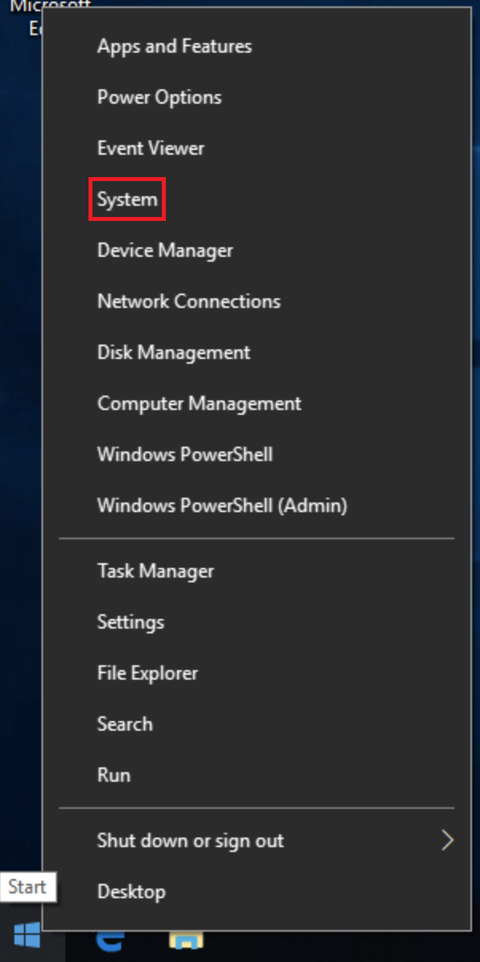
At the bottom of the Settings window, find and click the System info hyperlink:
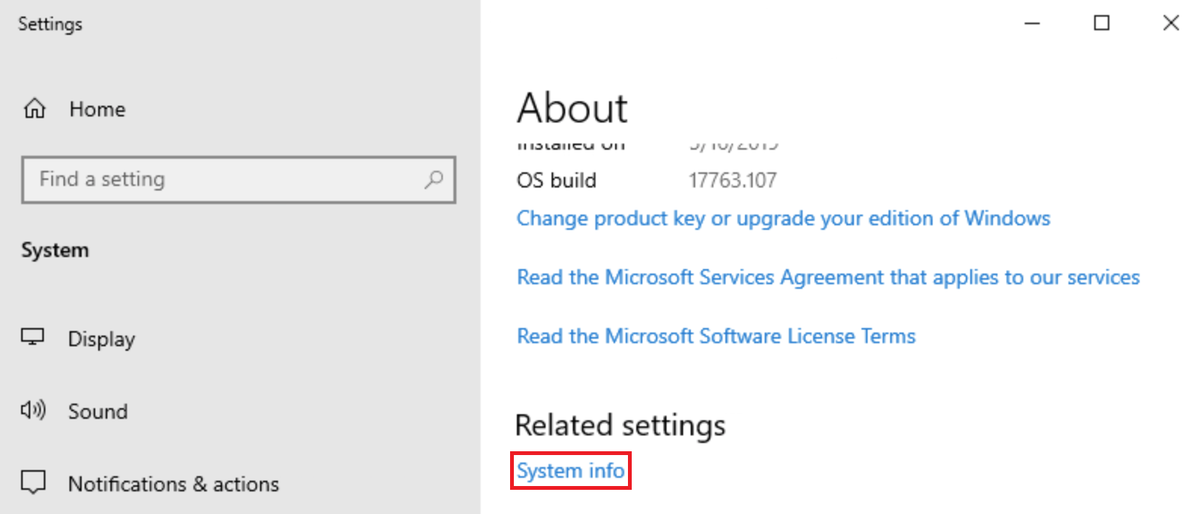
In the resulting window, click Change settings:
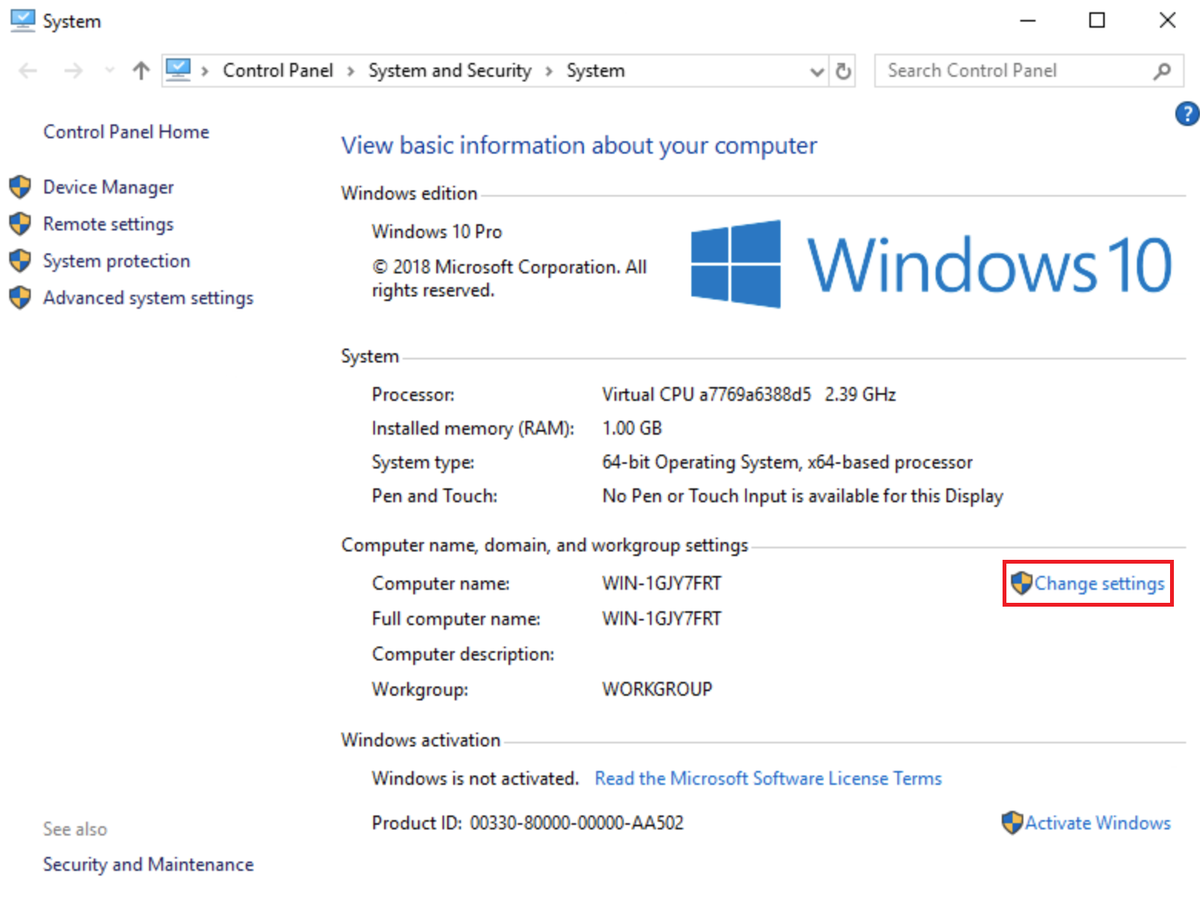
In System Properties, click Change:
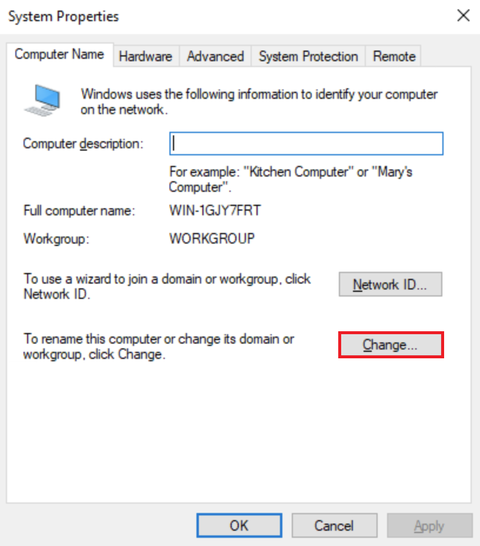
Enter the Computer Name and Domain, then click OK:
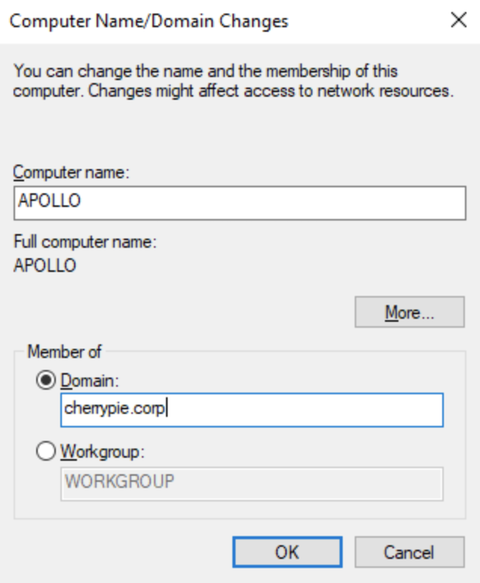
You should be prompted to enter domain credentials. Enter the domain admin username and password you previously created, then click OK:
Upon successfully connecting to the domain, you’ll be greeted with this dialogue:
Congratulations! The workstation is now part of the domain, and setup is complete.
Extra Credit
At this point, there is no further configuration required. However, it could be an idea to:
- Install all available Windows updates
- Adjust timezone
- Install antivirus
- Install a browser other than Internet Explorer
- Take a snapshot
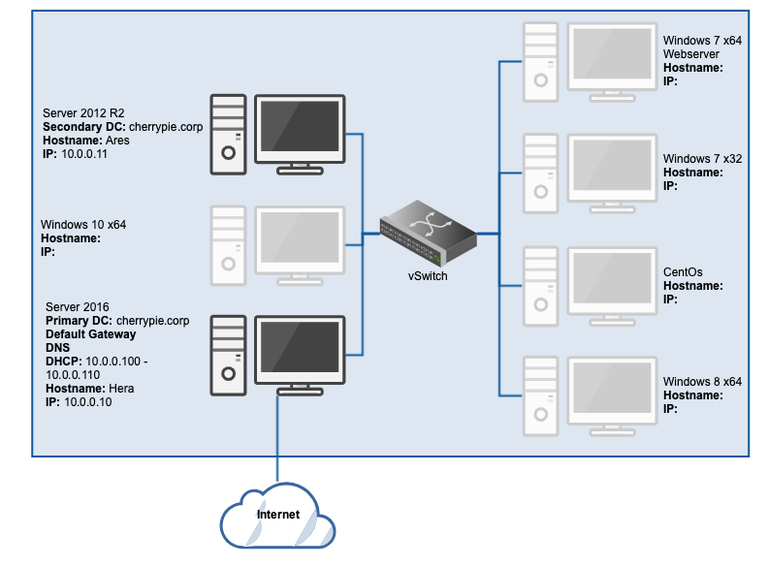
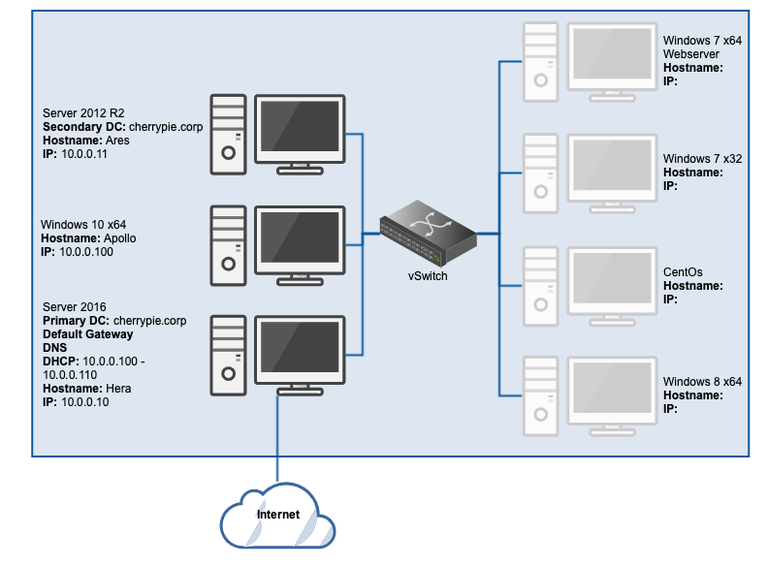
At the end of this process, the lab should look similar to this:
Go here to see how the Server 2012 R2 DC was created, or here to move on and create a Windows 8.1 workstation within the lab domain.