Create a Personal Forensics Lab Part 6: The CentOS Workstation
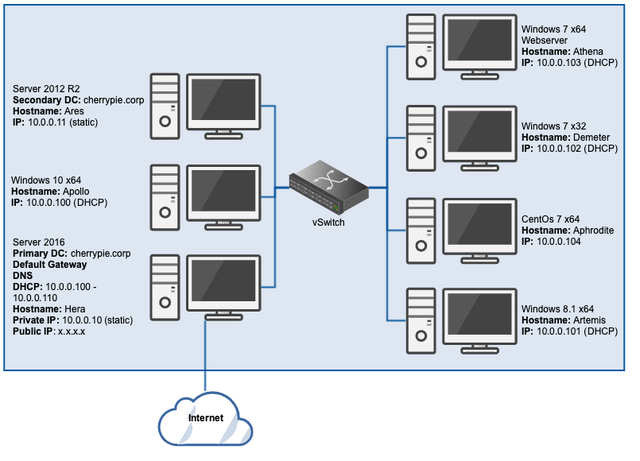
This (for now anyway) will be the last post in this series, in which we’ll add a CentOS 7 x64 workstation to our lab. At this point, the lab looks a little like this:
There are some slight nuances to adding a CentOS box to a Windows domain, and we’ll go into greater detail below. Similar to the other systems, we want CentOS in a DFIR lab for the opportunity to find artefacts, auth logs, time sources, etc.
For purposes of illustration, we’ll use the CentOS GUI for configuration. This is achieved at the command line by executing the following commands to install and enable the desktop.
Install the desktop:
yum groupinstall "GNOME Desktop" "Graphical Administration Tools"
Enable the desktop at startup:
ln -sf /lib/systemd/system/runlevel5.target /etc/systemd/system/default.target
Reboot.
Workstation Installation
The first step in installing CentOS 7 from the GUI is to select the language:
I chose English. Click Next. Select the relevant keyboard layout and click Next:
For testing purposes, I left Location Services on. This machine is a VPS anyway, so my physical location is irrelevant. Click Next:
Select any timezone you like, but probably the same as the other VMs in the lab. Click Next:
I skipped connecting any online accounts for now. If I want to test this in the future, I’ll likely create a testing account for whichever account(s) I’m testing. Click Skip:
On the following screen, there will likely be a Set Up Enterprise Login button at the bottom. This should not work by default, and CentOS will require further configuration to connect to the domain. So, continue setting up a regular workstation user on this VM. Click Next:
Enter a strong password (because CentOS won’t allow you to enter anything else), then click Next. Finally, click the big blue Start Using CentOS Linux button to go to the desktop.
Once at the desktop (you might need to close a GNOME Help screen), click Applications, then Terminal:
Enter the following commands to install the prerequisites necessary to join the server to a domain:
sudo yum install -y sssd realmd oddjob oddjob-mkhomedir adcli \
samba-common samba-common-tools krb5-workstation \
openldap-clients policycoreutils-python
If any dependencies are identified, install those as well.
At this point, only the public facing NIC of this VM is configured. The private NIC also needs to be configured.
For a VM hosted by Vultr, this is done by adding the following text to the /etc/sysconfig/network-scripts/ifcfg-eth0 file:
DEVICE="eth1"
ONBOOT="yes"
NM_CONTROLLED="no"
BOOTPROTO="dhcp"
IPV6INIT="no"
MTU="1450"
Add that to the file using your favourite text editor and save the file.
Reboot.
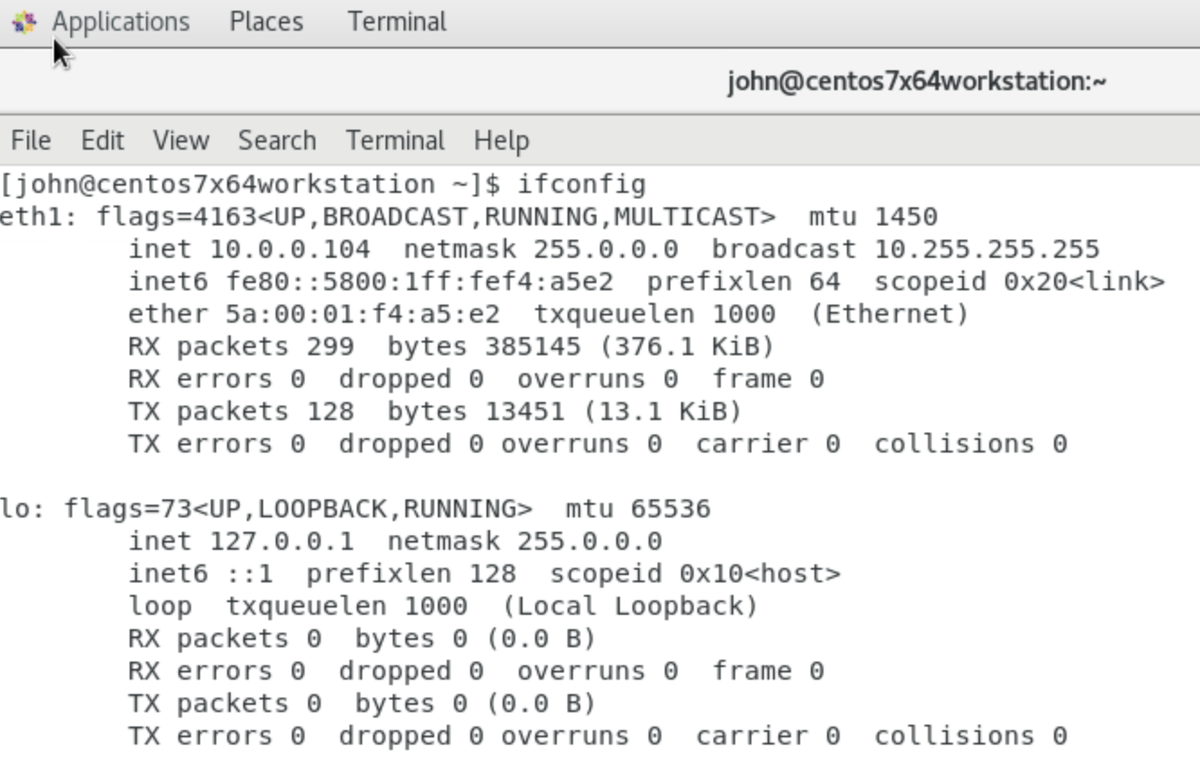
The VM should now be correctly configured for networking:
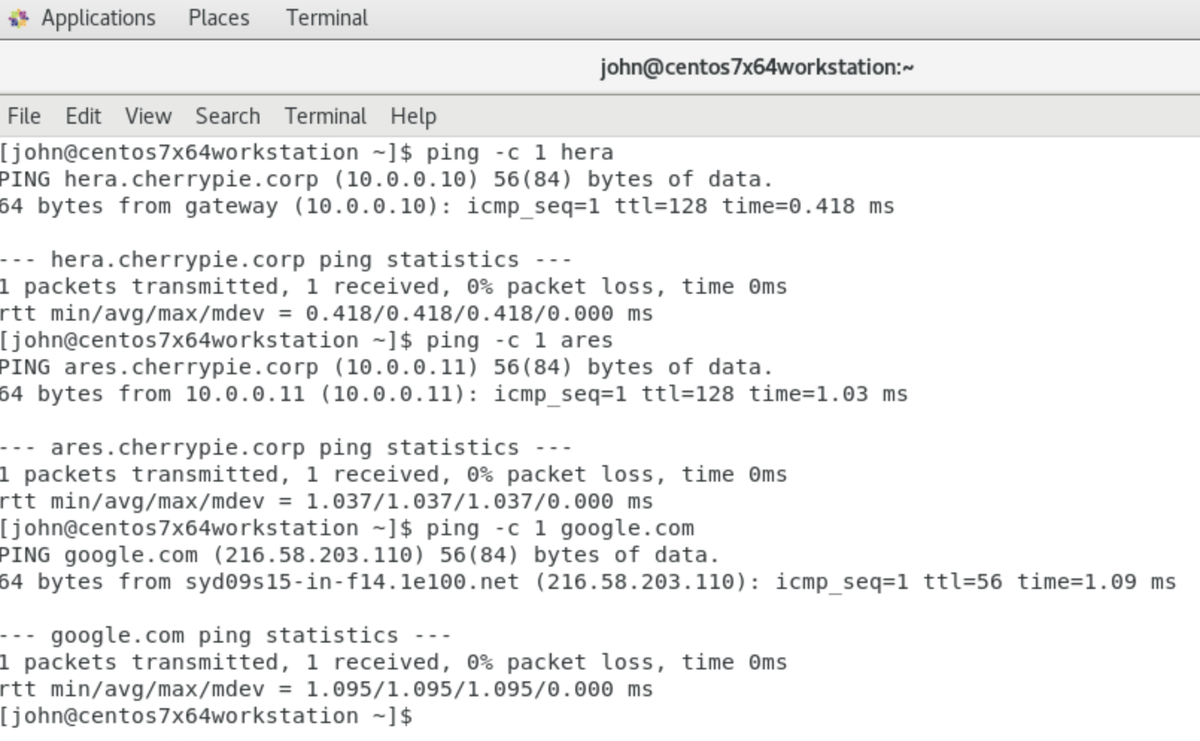
and be able to speak to the primary and secondary DCs, and the Internet:
It’s a good idea to update the hostname at this point as well:
sudo hostnamectl set-hostname aphrodite
This will also likely need to be updated in the /etc/hosts file, so open that with your favourite text editor and update it.
Domain Configuration
Run this command, replacing cherrypie.corp with the name of your domain and the username with your domain administrator username (note that it’s double-dash before the user option, not a single hyphen):
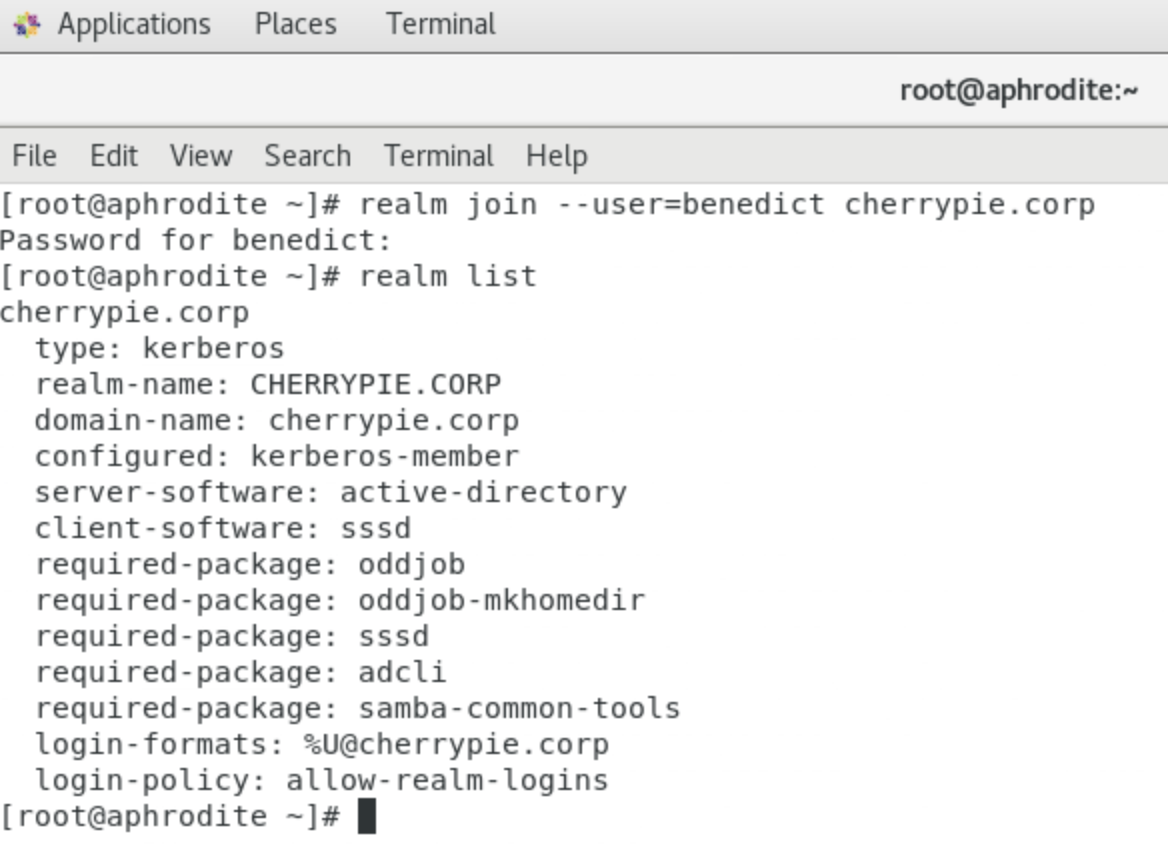
sudo realm join --user=benedict cherrypie.corp
NB: I had some trouble getting this to work. I had to sync the clocks of the DC and the CentOS VM; due due to the way Kerberos authentication works, anything greater than a five minute time difference will keep the two from connecting.
With the join command run successfully, the CentOS VM is now a part of the Windows LDAP domain. To check, run the realm list command:
Extra Credit
- Install all available updates (yum -y update)
- Take a snapshot
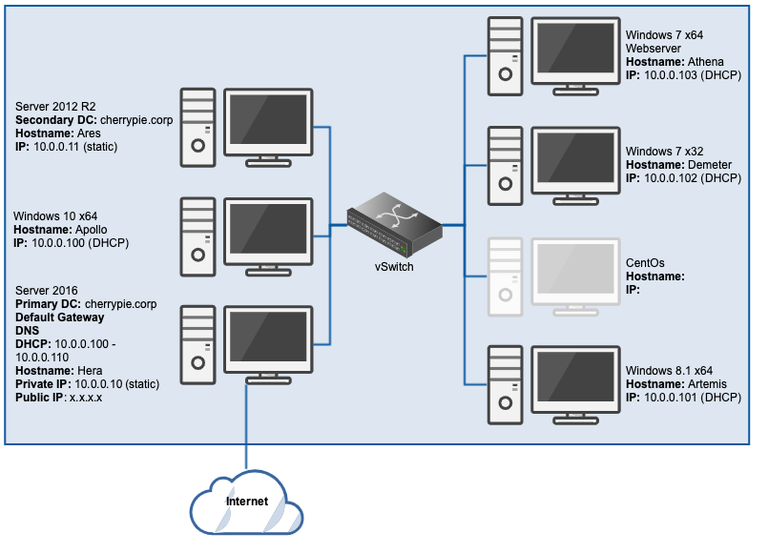
Now our completed lab looks like this:
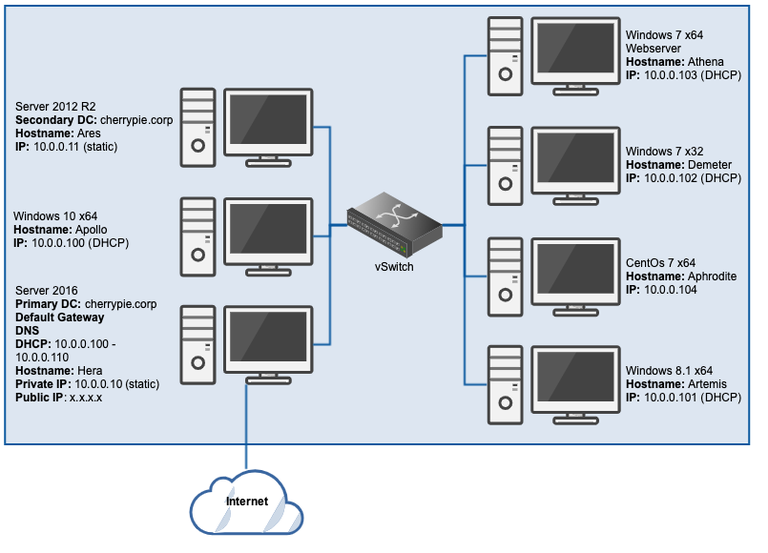
Now that we’ve created all the planned VMs, this lab is ready for testing.
Two things which are very instructive in terms of testing different operating systems and OS versions are:
- Recycle bin forensics
- Timestamp forensics
Both of these things change considerably between different versions of Windows, and Linux is an entirely different beast all on its own.
If you end up creating a lab similar to this and do any forensic testing, let me know what you get up to. I’m always interested in reading about interesting ‘features’ that can be used during investigations.
Happy hunting!